Information Security
Your Security is our concern !.
Every organization needs to protect its data and also control how it should be distributed both within and without the organizational boundaries.The evolution of computer networks has made the sharing of information ever more prevalent. Information is now exchanged at the rate of trillions of bytes per millisecond,
Information security policy is a set of policies issued by an organization to ensure that all information technology users within the domain of the organization or its networks comply with rules and guidelines related to the security of the information stored digitally at any point in the network or within the organization's boundaries of authority.
A typical security policy might be hierarchical and apply differently depending on whom they apply to. For example, the secretarial staff who type all the communications of an organization are usually bound never to share any information unless explicitly authorized, whereby a more senior manager may be deemed authoritative enough to decide what information produced by the secretaries can be shared, and to who, so they are not bound by the same information security policy terms.
Sensitive information refers to privileged or proprietary information that only certain people are allowed to see and that is therefore not accessible to everyone. If sensitive information is lost or used in any way other than intended, the result can be severe damage to the people or organization to which that information belongs.

Some examples of sensitive information are as follows:
- Personal information, including Social Security Number and bank credentials
- Trade secrets
- System vulnerability reports
- Pre-solicitation procurement documentation, including work statements
- Computer security deficiency reports
According the Computer Security Act of 1987, organizations must be held responsible for protecting their own sensitive information by providing one or more of the following:
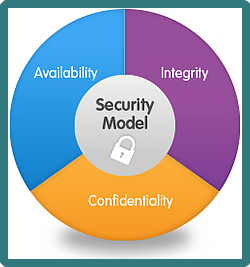
- Confidentiality: Sensitive information should only be accessible to those who are allowed to see it, not just those who wish to see it.
- Integrity: Unauthorized users should not be able to make changes to the information, thus compromising its integrity.
- Availability: Information must be accessible during a certain time and may not be destroyed during that time frame. People with permission to view the data must be able to view it.
We develop policies and procedures to avoid and keep track of unauthorized access, exploitation, modification, or denial of the network and network resources.
We protecting information systems through maintaining these five qualities of the system.
- Integrity
- Availability
- Authentication
- Confidentiality
- Nonrepudiation
